


Next: Revocation of Access Rights
Up: Capabilities
Previous: Capabilities
A server or manager issues capabilities to access the objects it controls,
such as file servers managing object files
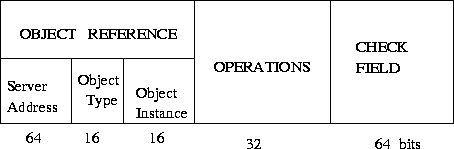
Figure 5: Capability in distributed systems
- Check field encrypted version of permitted operations field and a random constant
- Protects capability and prevents it being forged
- When object created, a random number generated and stored in an internal reference table
to the object
- When an access request received, the object field used as an index into the table
- Decrypting check field must yield the correct constant for the request to be permitted
- Creation, copying or modifying capabilities are protected OS operations
- Operations field indicates which of these operations are permitted on the capability itself
- Modifying operations field (usually to reduce access rights before passing on capability)
performed by requesting the originator to issue a new one (by a special commutative ONE WAY function
- Capabilities permit VERY LIMITED access rights to be passed to other users
- Check capabilities can be more efficient than ACLs - so are used when checking is needed for
each operation
Omer F Rana
Sun Feb 16 17:49:18 GMT 1997

