


Next: Protection Domain
Up: No Title
Previous: SECURITY
- Identification : Identify the user - who are you ?
General login id (name or number) supplied by user
what other methods exist ?
- Authentication : Verifying identity of user - Are you who you
say you are - Use of passwords (generally)
Check if user supplied password matches that stored in system
Check at login time / access to a resource (file)
stored passwords MUST be protected : encryption
Unix uses a one-way function for encoding passwords :
x 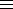 F(x) (easy to compute)
F(x) (easy to compute)
F(x) 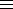 x (difficult or impossible to compute)
x (difficult or impossible to compute)
store F(x) NOT x (need to be protected)
Must prevent guessing passwords - max number of tries (3 attempts
at login)
- Authorisation : Specify who can access what - what operations
are permissible (based on policy decisions)
Default authorisation : no access ?, all access ?
- Principle of Least Privilege : Give user process the minimum
access rights required to carry out assigned task (- need to know basis!)
Omer F Rana
Sun Feb 16 17:49:18 GMT 1997